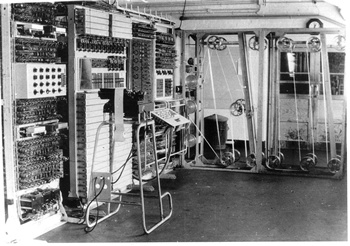
This picture is the fourth challenge, and is my favourite of the lot. Straight away you might be able to guess the answer, but it will reveal itself in due time.
Hiding in Plain Sight(top)Hiding things in images is not a new thing, there are all sorts of presentations and white papers on it - in fact it's been shown to be a good attack vector for hacking computers.
The easy thing to check is the EXIF data attached to the image:
$ exiftool comp3.jpg
ExifTool Version Number : 9.13
File Name : comp3.jpg
Directory : .
File Size : 61 kB
File Modification Date/Time : 2013:09:14 23:03:53+01:00
File Access Date/Time : 2013:10:24 22:17:43+01:00
File Inode Change Date/Time : 2013:09:14 23:03:53+01:00
File Permissions : rw-rw-r--
File Type : JPEG
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : inches
X Resolution : 200
Y Resolution : 200
Image Width : 350
Image Height : 246
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:4:4 (1 1)
Image Size : 350x246
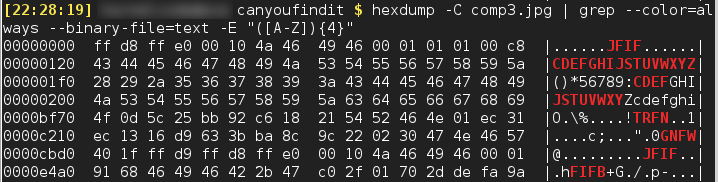
That doesn't really tell us anything interesting. I guess that would be too easy. Next I checked the file for any obvious text strings hidden in it's binary code. Using hexdump and grep (you do know how to use grep by now right? If not, learn it!) I didn't spot any obvious long web-address like strings, but I did find something interesting.
The Solution(top)This command finds sequences of 4 capital letters - I have specifically used it here to illustrate the point with a minimum of noise. It wasn't the first thing I tried!
Ignore the sections of the alphabet - they're just parts of the file which happen to contain sequential numbers corresponding to capital letters.
Anyway, notice that on the first line we have "JFIF" and on the last-but-one line we have "JFIF" again...
JFIF stands for JPEG File Interchange Format, and if you have a look at Wikipedia it has a breakdown of the markers used in the JPEG file format. A JPEG file always starts with 0xFFE0, then a 16 bit field, then JFIF - a sort of magic number the computer can look for to determine that the file is a JPEG.
What's strange is, our picture seems to have a second one of these at the end of it? In fact, if you look a little closer, it comes immediately after 0xFFD9, which marks the end of the image, and the file terminates with another 0xFFD9. In short, the image we downloaded from the website has a second image stuck on the end of it!
Most (all?) image viewers will read from the start of a file until they reach to 0xFFD9 marker and then stop, assuming that's the end of the file. So now we have to cut the second image off the end of the file and have a look at it
I used dd, which is a generic binary stream copier. I basically told it to take all the bytes starting at the start of the second image, and put them into a new file:
$ dd ibs=1 skip=52180 count=10288 if=comp3.jpg of=comp4.jpg
The command basically says "working one byte at a time, starting at position 52,180 in comp3.jpg, copy 10,288 bytes to comp4.jpg". The offset 52,180 corresponds to the start of the second image, hex address 0xCBD4. 10,288 is all the bytes that are left - the file size is 62,468; (62,468 - 52,180) = 10,288.
So there we have it! This image was hidden at the end of the one we downloaded from the website and clearly contains our next clue, www.eveningstandard.co.uk/colossus. The 4th answer is colossus, which is actually the computer in the first picture - it was used at Bletchley park during WWII to help crack the Lorenz cipher.
So that's that, probably the easiest challenge so far - let's take a look at Challenge 5.